Enterprise grade security & compliance
At GetAccept, security isn’t an afterthought—it’s built into the very core of our platform. We leverage industry-leading encryption, continuous monitoring and alerts, and proactive measures such as daily backups to protect your data at every stage.

Trusted by leading enterprises worldwide
Comprehensive security & compliance at a glance
GetAccept delivers a complete security ecosystem engineered for today’s enterprise challenges. We meet and exceed global standards—from GDPR and SOC 2 to eIDAS—ensuring your sensitive data is secure, compliant, and always available.
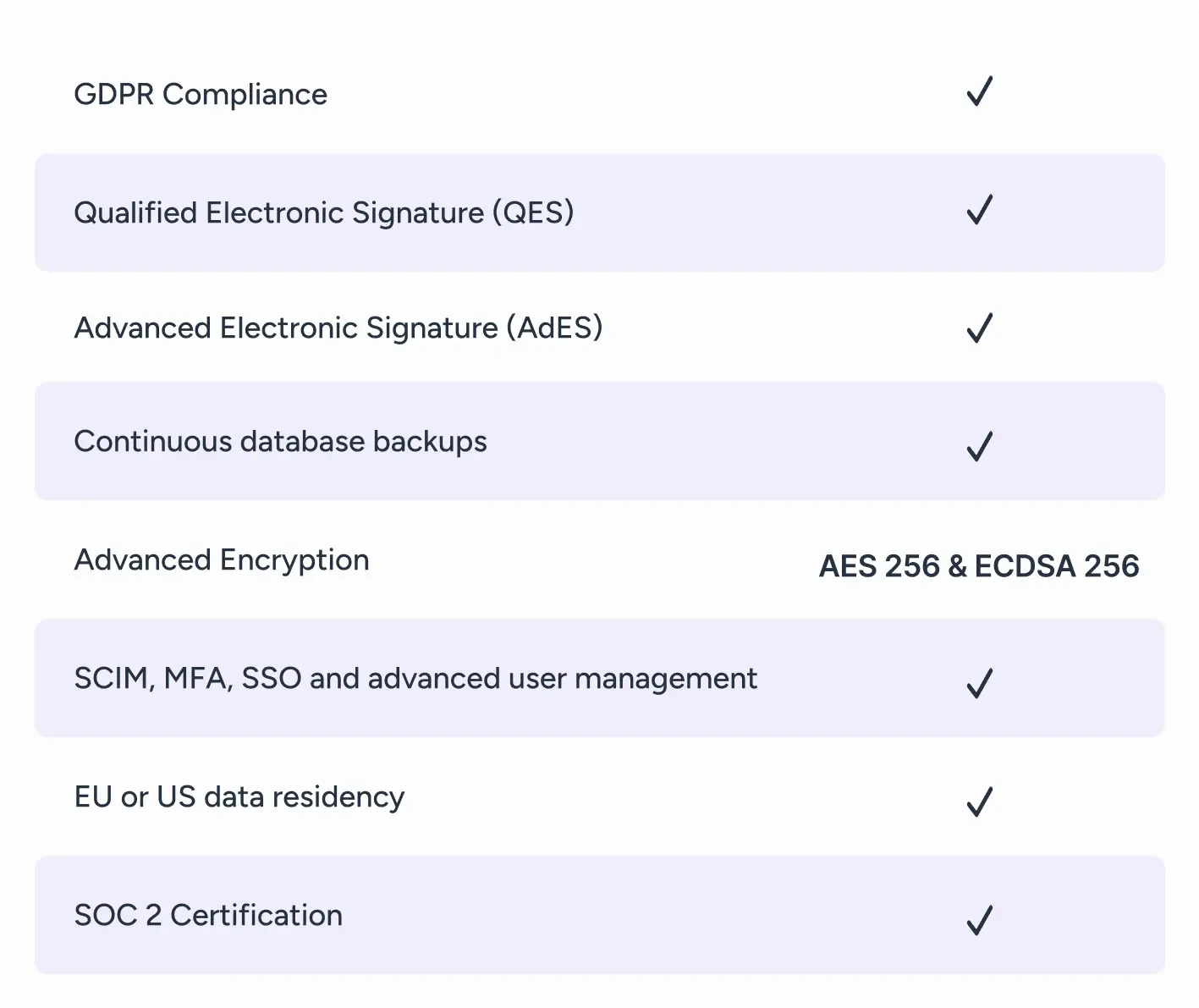
Robust product security features
-

Granular user management
Control access at a granular level with role-based permissions that align with your internal security policies.
-

SCIM integration
Streamline identity management across your IT ecosystem with automated user provisioning and deprovisioning.
-

Multifactor authentication
Strengthen account security with MFA for both internal users and external recipients, adding a critical layer of protection.
-

Single Sign-On (SSO)
Integrate seamlessly with all SSO providers thanks to our standard SAML connector —including Azure, Okta, OneLogin, and Google
-

Data retention
Configure data policies to enforce compliance requirements, ensuring data is securely stored and timely deleted according to your policies
Every company has different security needs. Let's get specific!
GDPR / CCPA Compliance & privacy by design
Designed with a privacy-first approach, GetAccept ensures your data is processed and stored securely in full compliance with Europe’s GDPR and California's CCPA regulation. We enable you to manage consent, uphold data subjects’ rights, and implement robust data protection measures—all built into our platform by design.

Advanced and Qualified electronic signature support (AdES, QES)
Secure your digital signatures with GetAccept’s comprehensive eSignature solutions that fully adhere to the eIDAS regulation. Whether you need, basic, advanced or qualified electronic signatures, our platform ensures every signature is legally binding through multiple authentication options such as security questions, SMS verification, and eID-based authentication.

Enterprise grade platform security and SOC 2 certified
GetAccept is built on a stable, redundant and scalable infrastructure and designed for 100% uptime. We have backups, full encryption and conduct yearly penetration tests to secure data against all possible threats.
- ECDSA 256 & AES 256 Encryption
- Carefully selected shortlist of data sub processors
- SOC 2 Certification and rigorous yearly audit
- Regular security training for our staff

Infrastructure and networking
At GetAccept, our systems run on updated Linux servers and hardened cloud services (e.g., Amazon RDS, S3). Our robust network delivers secure, reliable performance to meet enterprise demands.
Data storage and protection
We manage your document data across fortified locations. Every store is encrypted with AES-256 and protected by advanced key management to ensure confidentiality and integrity.
Controlled personnel access
GetAccept enforces strict access controls. Our teams receive only the permissions they need, minimizing risk and ensuring data interactions adhere to rigorous security protocols.
Segregated environments
Our production systems are isolated from corporate, QA, and development networks. This segregation reduces risk by ensuring each environment operates independently and securely.
Secure handling of payment data
For payments, GetAccept partners with trusted third-party providers. We never store or process sensitive card data, keeping transactions secure and fully compliant.
Continuous surveillance and alerts
We monitor all applications and infrastructure 24/7. Automated systems detect anomalies and escalate alerts to our on-call team for swift action on any security events.
High availability and backup procedures
We ensure constant service using auto-scaling, load balancing, and rolling deployments. Daily, encrypted database backups offer robust protection and reliable data recovery.
Rigorous security assessments
Our development cycle includes thorough security testing with advanced tools and scans. We proactively identify and resolve vulnerabilities before deploying new features.
Layered system architecture
GetAccept is built on a multi-tier design separating the front-end, logic, and database layers. This DMZ-like structure ensures each layer is independently secured.
Learn more about our security engagement

Our privacy policy
We take your safety seriously. Read GetAccept's privacy policy here! GetAccept helps clients close more deals by sending personalized content.

Data Processing Agreement
Explore our Data Processing Agreement to see how we securely handle, process, and protect your data with full transparency and strict compliance measures

Electronic Signatures & eIDAS
What is an electronic signature? Learn how e-signatures work, why they’re secure and legal, and how they help you close deals faster.